Discover how cyber adversaries evolve their tactics and explore the intricate techniques attackers use to escalate privileges, establish persistence, and maintain stealthy command-and-control (C2) channels. From webshells to sophisticated post-exploitation frameworks, gain insights into the latest threat actor strategies and how defenders can stay ahead. Whether you’re a cybersecurity professional or an enthusiast, this deep dive into modern cyber threats is a must-read.
For more information, please check out the blog on our community page.
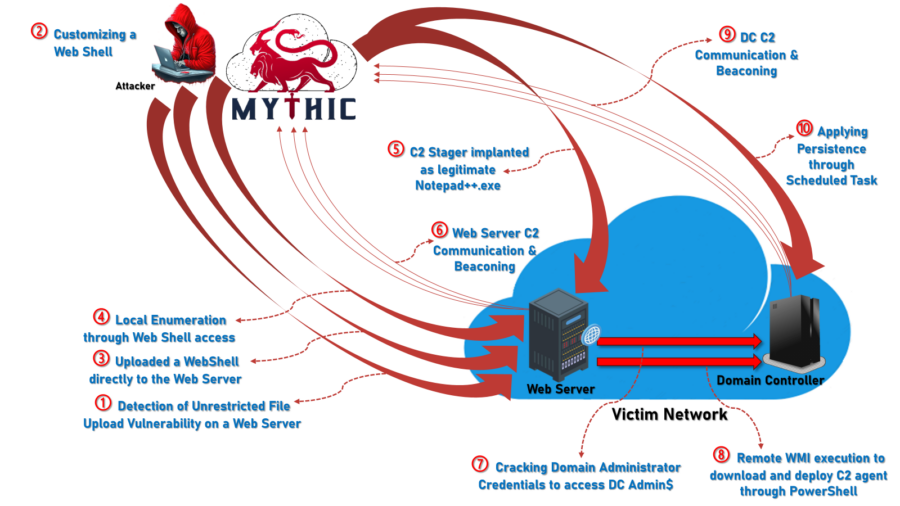
Figure 1: Attack Overview



