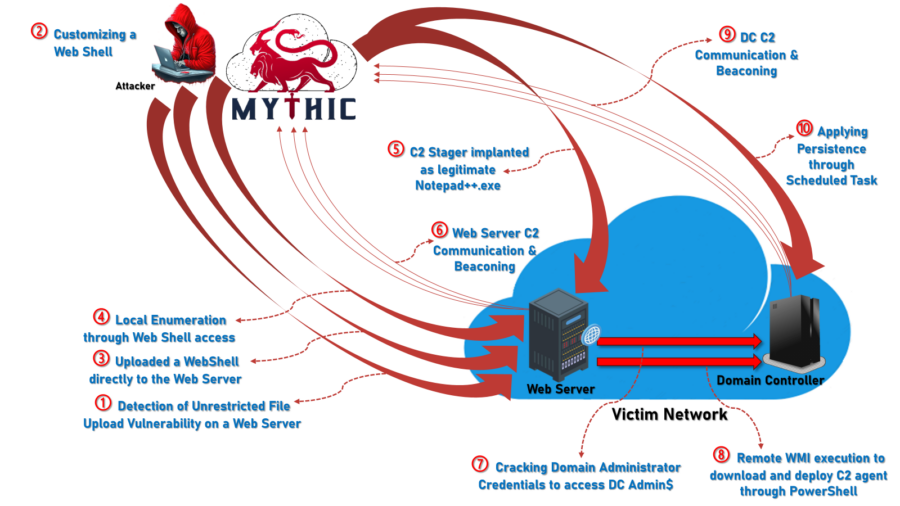
From Webshell to C2: The Evolution of Post-Exploitation and Covert Operations
From webshells to sophisticated post-exploitation frameworks, gain insights into the latest threat actor strategies and how defenders can stay ahead.
Read more
From webshells to sophisticated post-exploitation frameworks, gain insights into the latest threat actor strategies and how defenders can stay ahead.
Read more
2024 saw significant global events – from the Paris Olympics to medical breakthroughs – but it also brought concerning cyber incidents, particularly the Salt Typhoon attacks targeting U.S. telecommunications. This sophisticated, nation-state-backed group (linked to China’s MSS) exploited vulnerabilities across industries, wreaking havoc on sensitive infrastructure. Dive deep into this breach, gaining insights and recommendations to help organizations navigate and mitigate future risks.
Read more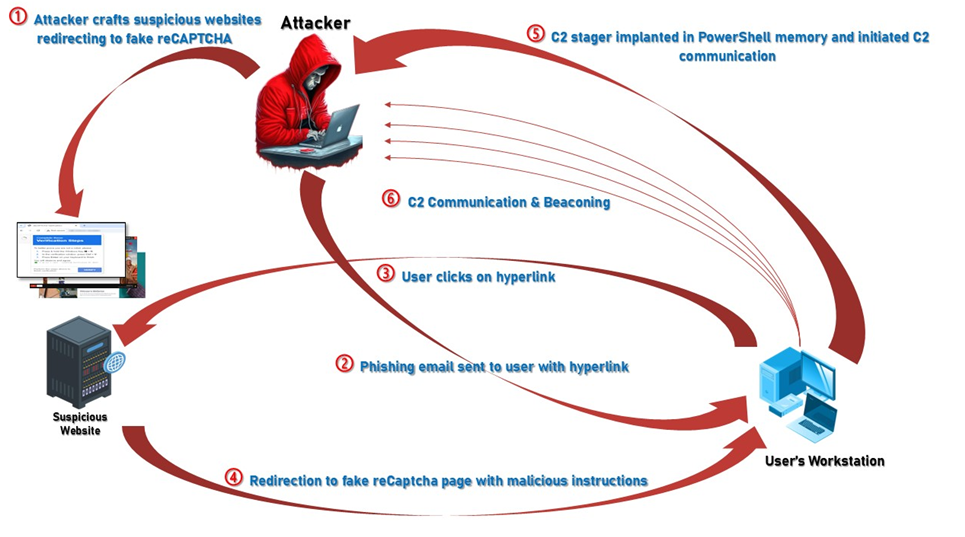
By leveraging NetWitness Packets (NDR) and NetWitness Endpoint (EDR), the NetWitness Incident Response team demonstrates how organizations can detect stealthy reCAPTCHA phishing attacks before they cause irreparable harm.
Read more
Introduction Much discussion has occurred in recent years concerning cybersecurity in and related to IOT and OT environments. Traditionally, these areas of concern have been largely kept separate from “corporate” or “enterprise” networks and environments due in large part — though not exclusively, to the sensitive operating nature of the environments where these technologies are […]
Read more
NetWitness is happy to be part of the NOC again for another global event by Black Hat in Singapore. The Black Hat Network Operations Center (NOC) delivers a secure, reliable network in one of the most challenging environments in the world. This is done with the support of top-notch solutions providers and experienced security and […]
Read more
Since cybersecurity is an ever-evolving field, staying abreast of cutting-edge technologies and frameworks is necessary for organizations aiming to strengthen their defenses against an array of threats. Two prominent paradigms that have emerged as game-changers in the realm of network security are Secure Access Service Edge (SASE) and Secure Service Edge (SSE). In this comprehensive […]
Read more
Within the realm of data management and cybersecurity, the integration of cloud analytics has become a transformative force for organizations looking to maximize the potential of their digital infrastructure. This era is marked by the rise of cloud analytics as a catalyst, empowering organizations to gain actionable insights from vast datasets. NetWitness, a standout player […]
Read more
Behind the scenes at Black Hat USA 2023, Network Operations Center (NOC) partners watch and wait, scanning the event’s network for suspicious activity. But with over 20,000 cyber enthusiasts and professionals in attendance, protecting the network is no easy task. Every year, the NOC partners are selected by Black Hat to provide a high security, […]
Read more
In today’s digital age, where data breaches and cyberattacks are on the rise, reliable cybersecurity is more important than ever. Among the many tools and techniques available to safeguard your organization’s digital assets, log management stands out as a cornerstone of effective cybersecurity. In this comprehensive guide, we will explore the significance of log management […]
Read more
A closer look at the features and strengths of our market-leading cybersecurity products. Keeping pace with leading cybersecurity solutions and industry evaluations is essential—but it isn’t always easy. Fortunately, resources like the GigaOm Radar Report, which analyzes top-performing tools, can serve as an authoritative guide for IT professionals and decision-makers. This year’s Radar Report includes […]
Read more